On May 22, 2025, the Cetus Protocol, one of the most prominent DEXs on Sui and Aptos blockchains, faced its most serious challenge in history. A major security breach led to the loss of over $260 million in digital assets, making it one of the largest DeFi exploits in history.
The attacker used spoof tokens to exploit a flaw in the Cetus
smart contracts, draining liquidity pools and shaking confidence in the
Sui ecosystem. The fallout impacted not only CETUS token holders but also triggered a broader debate about decentralization,
validator control, and smart contract security.
For anyone active in crypto, this hack is a wake-up call, and a key case study for understanding the risks and resilience of DeFi infrastructure.
What Is Cetus Protocol DEX and How Does It Work?
Cetus Protocol is one of the most prominent decentralized exchanges (DEXs) on the
Sui and
Aptos blockchains - two fast, scalable
Layer 1 networks designed for Web3 applications. As a DEX, Cetus allows users to swap tokens, provide liquidity, and earn trading fees in a
non-custodial, permissionless environment. Known for its advanced trading features and flexible
liquidity options, Cetus has played a key role in powering
DeFi activity on these emerging networks. By offering tools like programmable swaps and concentrated liquidity pools, the platform has attracted thousands of users and developers across the
Web3 space.
At the core of Cetus lies its Concentrated Liquidity Market Maker (CLMM) model, a feature popularized by
Uniswap V3. Unlike traditional automated market makers (
AMMs) that spread liquidity evenly across all price points, CLMM lets liquidity providers (LPs) choose specific price ranges for their positions. This gives LPs more control, allows for tighter spreads, and helps maximize capital efficiency.
Cetus takes the CLMM model further by offering programmable trading tools, composability for
dApp developers, and a dual-token system (CETUS and xCETUS) to reward long-term participation. With these features, Cetus has become a go-to DEX for users seeking faster execution, lower slippage, and more customizable DeFi strategies on Sui and Aptos.
Key Features of Cetus Protocol
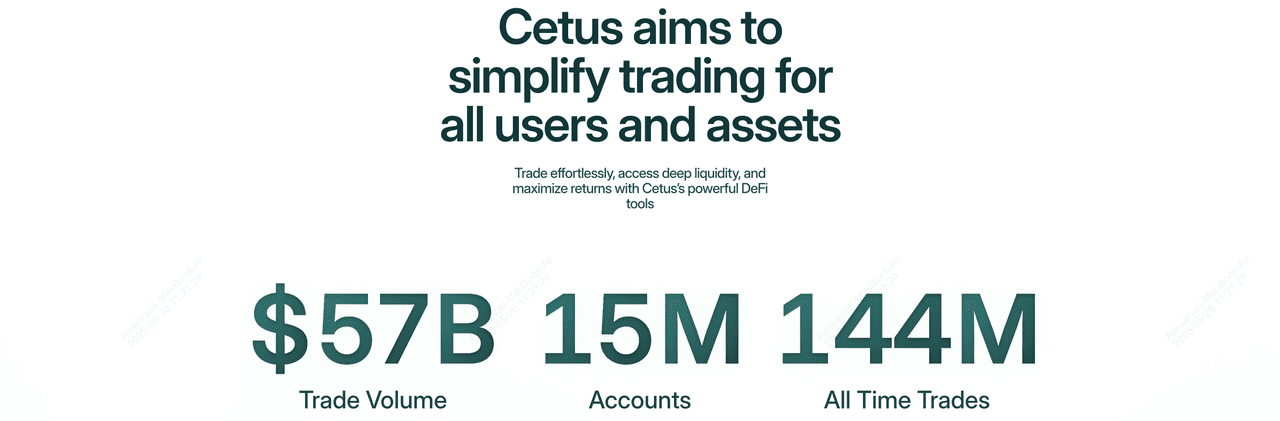
An overview of Cetus Protocol | Source: Cetus.zone
With the following capabilities, Cetus isn't just a trading platform - it's an entire liquidity infrastructure optimized for the next generation of decentralized finance.
• Concentrated Liquidity (CLMM): LPs can deploy capital within custom price ranges to earn more fees and reduce idle liquidity.
• Permissionless and Open Access: Anyone can create liquidity pools, deploy trading strategies, or build on top of Cetus.
• Programmable Trading Strategies: Traders can execute
limit orders, range orders, and other advanced tactics using on-chain tools.
• Liquidity as a Service (LaaS): Projects can tap into Cetus liquidity through its SDK, making it easy to launch vaults,
derivatives, and yield strategies.
• Dual Token Model: The protocol uses
CETUS token for utility and xCETUS for governance and staking rewards.
• Built for Integration: Cetus is developer-friendly, offering seamless composability with other DeFi apps and protocols.
• High-Speed Performance: Built on Sui and Aptos, Cetus supports low-latency, high-throughput trading ideal for modern DeFi.
A Recap of The Cetus Protocol Breach: Everything You Need to Know
On May 22, 2025, Cetus Protocol was hit by one of the most severe security breaches in DeFi history. The exploit resulted in the loss of over $260 million, primarily in SUI,
USDC, and other assets across multiple liquidity pools on the platform.
The attacker used a technique known as
oracle manipulation. This exploit targeted the internal pricing mechanism of Cetus, which relies on pool data rather than external oracles. The vulnerability was tied to how the protocol calculated asset values inside its smart contracts, specifically within functions that handled liquidity math and pricing curves.
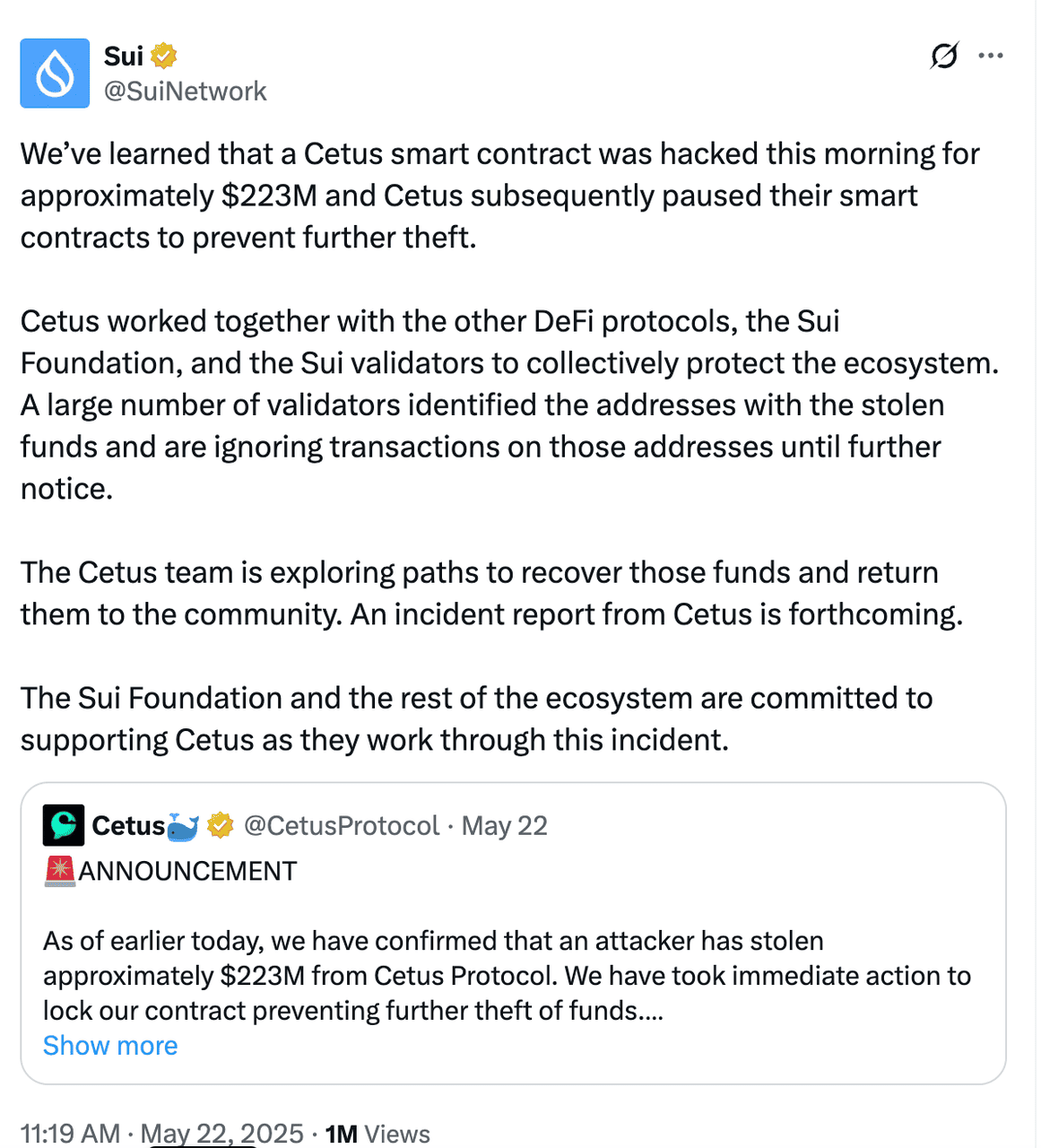
The official announcement about the Cetus exploit | Source: Cointelegraph
To carry out the attack, the hacker deployed spoof tokens - fake assets with little or no actual value. These tokens were introduced into the pools to distort pricing curves and reserve balances. By faking token values and exploiting a flaw in Cetus's overflow check, the attacker was able to trick the protocol into releasing large amounts of real assets in exchange for worthless ones.
At its core, this was not a traditional smart contract bug but a logic flaw in the AMM math. It allowed the attacker to add massive amounts of liquidity with minimal input and withdraw valuable tokens like SUI and USDC without contributing proportional value. On-chain activity spiked dramatically, with over $2.9 billion in transaction volume recorded on May 22, up from just $320 million the previous day.
What Happened After the Cetus Protocol Security Breach?
As soon as the exploit was detected, the Cetus team acted quickly. All smart contract operations were immediately paused to prevent further damage, and the team launched an internal investigation into the breach. A statement was published on Cetus Protocol’s official X (formerly Twitter) account, confirming the incident and urging users to stay informed as the team worked on a recovery plan.
Within hours, $162 million of the stolen assets were frozen thanks to a coordinated effort between Cetus, the Sui Foundation, and the network’s validators. The stolen funds were traced and locked on-chain, preventing the attacker from moving or off-ramping a large portion of the assets.
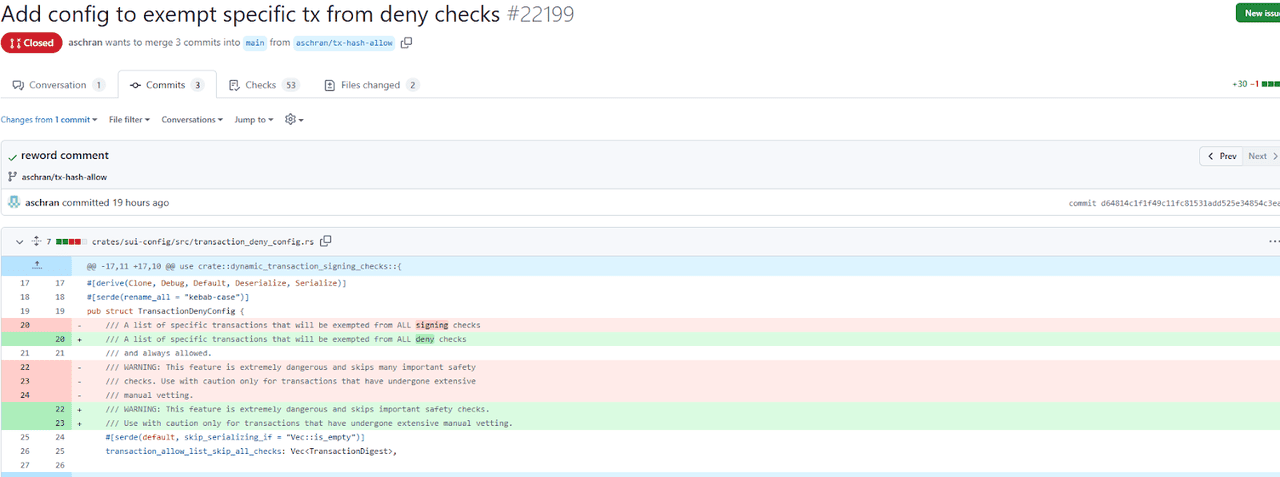
Mysten, Sui white list function | Source: Cointelegraph
To aid recovery efforts, Cetus offered a
$6 million white-hat bounty to the hacker. The deal: return the stolen funds and walk away with 2,324
ETH as a reward, no legal action pursued. As of the latest update, there has been no public response from the attacker, but the frozen funds remain under watch, and negotiations with third-party security firms and law enforcement are ongoing.
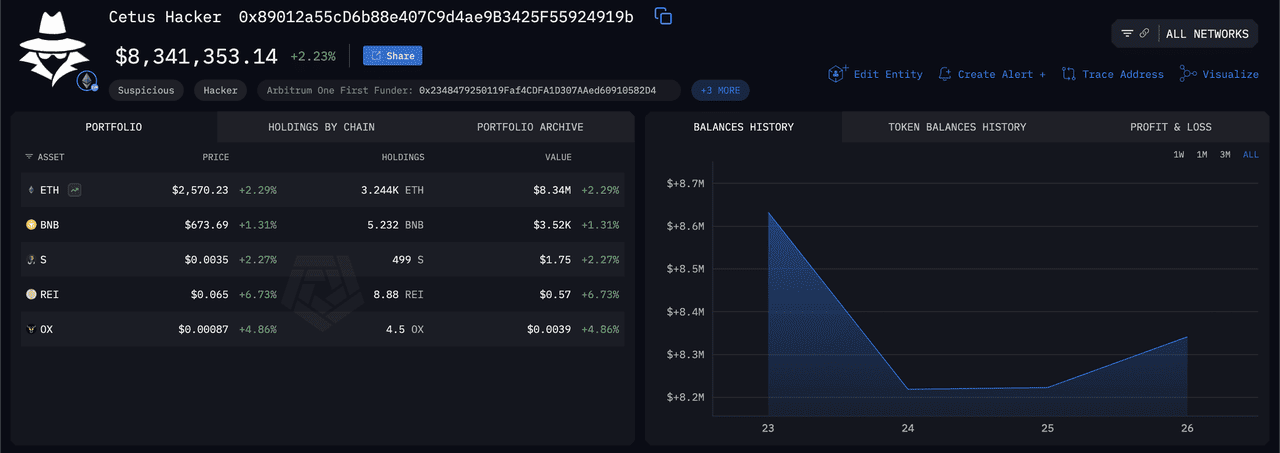
The Cetus hacker's funds | Source: Arkham Intelligence
This swift response helped contain the crisis, but it also sparked a deeper conversation across the crypto market about decentralization, censorship, and the power that blockchain validators can exercise in times of emergency.
CETUS Token Crashed 40% in 24 Hours After the Security Breach Before Recovery
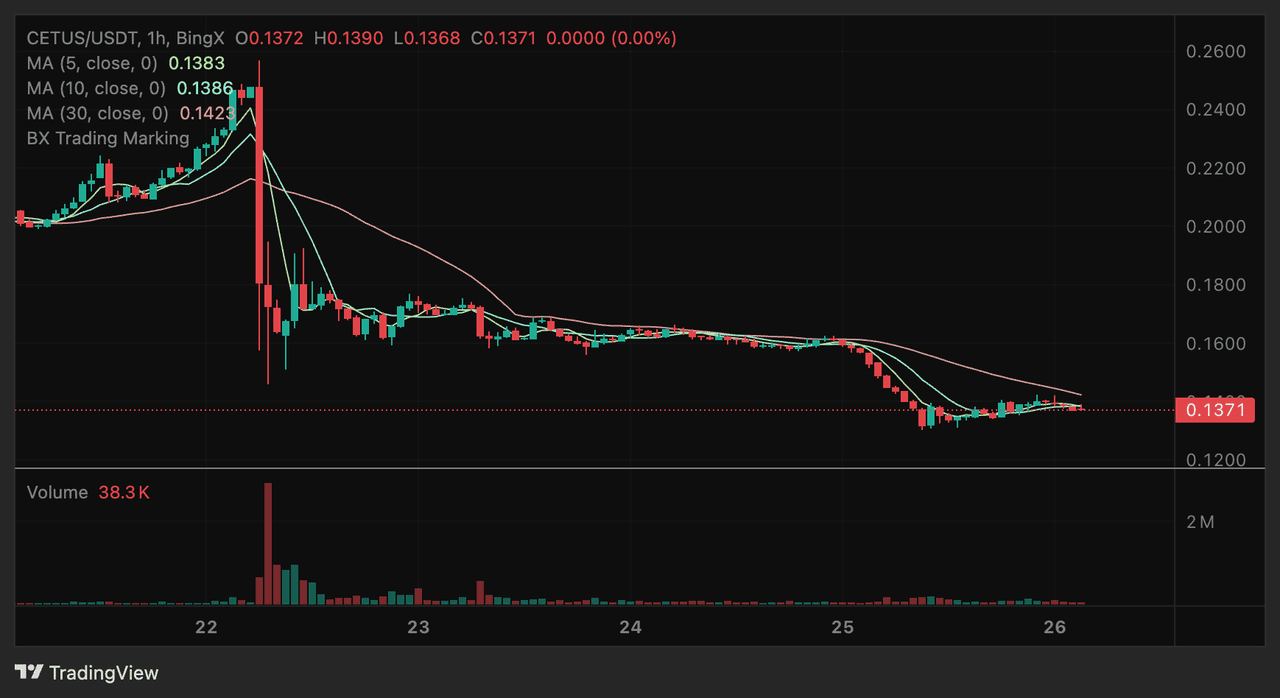
CETUS token market performance | Source: BingX
The Cetus Protocol hack on May 22, 2025, caused shockwaves across the Sui ecosystem and the broader DeFi market. Following the exploit, CETUS, the native token of the protocol, fell sharply from $0.26 to $0.15, a drop of over 40% in under 24 hours. SUI, the token powering the Sui blockchain, also lost nearly 14%, sliding from $4.19 to $3.62 amid fears of systemic risk and declining confidence in on-chain security.
However, in the days following the incident, both tokens showed signs of recovery. As of this writing, SUI is hovering near $3.64, and CETUS has stabilized around $0.13, after dipping even lower during the immediate aftermath. While not fully recovered to pre-hack levels, the rebound suggests that investor sentiment is slowly improving, helped by the protocol’s rapid response and partial fund recovery.
Trading volume on Cetus spiked from $320 million to over $2.9 billion on the day of the hack, driven by exploit transactions and panic withdrawals. The ripple effects were widespread. Smaller tokens listed on Cetus, including LBTC, AXOLcoin, and SLOVE, saw losses ranging from 50% to nearly 99%. Some assets temporarily lost nearly all their value due to cascading liquidity exits and pool imbalances.
The breach also caused a temporary depegging of USDC, exposed vulnerabilities in Cetus’s smart contract logic, and led to a $200 million+ drop in total value locked (TVL) on the Sui blockchain. Although $162 million in stolen assets were successfully frozen by Sui validators, concerns emerged about validator power and decentralization after transactions from attacker-linked
Sui wallets were blocked.
Meanwhile, the Cetus team has launched a dual-track recovery plan, offering a $6 million bounty to the hacker and initiating a community vote to authorize fund return protocols, aiming to restore user trust and protocol integrity. As recovery efforts continue, both CETUS and SUI are being closely watched, not only as investment assets but as indicators of how resilient emerging DeFi ecosystems can be in the face of high-stakes exploits.
The Cetus Hack Controversy: Decentralization vs. Emergency Intervention
One of the biggest controversies surrounding the Cetus hack wasn’t just the exploit itself - it was the response. Specifically, the freezing of $162 million in stolen funds by Sui validators sparked a heated debate over what decentralization really means in practice.
On one hand, many applauded the swift action. By working together, the Cetus team, the Sui Foundation, and validators were able to track and lock down most of the stolen assets within hours. This helped protect users and gave the protocol a fighting chance to recover. Supporters argued this was a real-world example of decentralization working as a coordinated, community-led defense system.
But not everyone agreed.
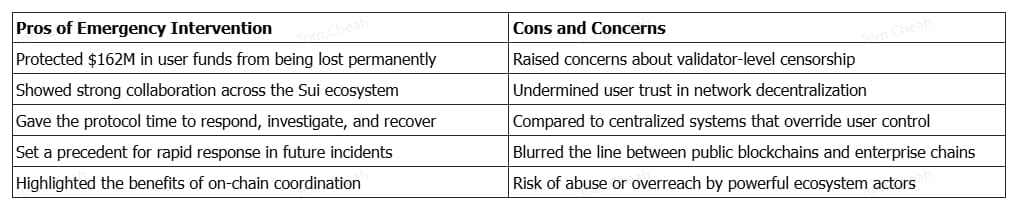
Pros and cons of emergency intervention after the Cetus Protocol hack
Critics pointed out that freezing wallet addresses, even those linked to hackers, raised serious centralization concerns. If validators can unilaterally block transactions or seize assets, does that mean users truly control their funds? And if a blockchain can override smart contract behavior during a crisis, how different is it from traditional financial systems?
Some compared Sui to an “enterprise blockchain”, claiming its validator structure gave too much control to a small group of actors. Others argued that decentralization doesn’t mean inaction; it means responsible governance, especially when user funds are at risk.
This event has forced the crypto community to confront a difficult question: Can a network be decentralized and still intervene during emergencies? Or does any form of control defeat the purpose of permissionless, unstoppable code?
The answer isn’t clear yet. But the Cetus hack has made the conversation impossible to ignore.
Lessons Learned and Future Precautions
The Cetus Protocol hack is a clear reminder that security must be a top priority in DeFi. Even well-designed platforms can suffer major losses if a single vulnerability goes unnoticed. In this case, a flaw in liquidity math led to a $260 million exploit, one of the largest in 2025. So, how can DeFi builders and users better protect themselves going forward?
For DeFi Developers: How to Build More Secure Protocols
• Conduct multiple smart contract audits with independent, experienced firms.
• Use formal verification for key calculations, especially in AMMs and liquidity logic.
• Implement circuit breakers to pause activity during abnormal trades or volume spikes.
• Rely on well-tested oracles and avoid internal-only pricing mechanisms for critical functions.
For DeFi Users: How to Stay Safe
• Check for audit reports and look into how a protocol has responded to past issues.
• Avoid overexposure by diversifying across multiple platforms.
• Use secure wallets and enable two-factor authentication (2FA) wherever possible.
• Stay informed about the protocols you use, including reading updates and community feedback.
In Web3, one of the best ways to reduce risk is to stay informed and proactive. Whether you're building or participating, security awareness is essential to navigating the DeFi landscape responsibly.
Conclusion
The Cetus Protocol hack, which resulted in losses exceeding $260 million, exposed a critical vulnerability in the platform’s liquidity logic. Although a large portion of the stolen funds was quickly frozen through coordinated efforts, the incident had a significant impact on market confidence and raised broader concerns about the security of DeFi protocols.
As decentralized finance continues to grow in complexity, so do the risks. This event underscores the importance of ongoing improvements in smart contract auditing, governance transparency, and emergency response strategies. Both developers and users have a role to play - through building with security in mind and staying informed about how protocols operate and manage potential threats.
Related Reading
 An overview of Cetus Protocol | Source: Cetus.zone
An overview of Cetus Protocol | Source: Cetus.zone The official announcement about the Cetus exploit | Source: Cointelegraph
The official announcement about the Cetus exploit | Source: Cointelegraph Mysten, Sui white list function | Source: Cointelegraph
Mysten, Sui white list function | Source: Cointelegraph The Cetus hacker's funds | Source: Arkham Intelligence
The Cetus hacker's funds | Source: Arkham Intelligence CETUS token market performance | Source: BingX
CETUS token market performance | Source: BingX Pros and cons of emergency intervention after the Cetus Protocol hack
Pros and cons of emergency intervention after the Cetus Protocol hack